Email scammers targeting SMBs under guise of accounting software
Forever popular with cybercriminals, this week has seen a series of email scams going directly for the money jar.
Leveraging major accounting software brands that are popular with the SMB segment – like MYOB, Xero and Sage – the cybercrime networks may be chasing smaller businesses who don't have a dedicated infosec or IT team to help defend against scams.
Starting at 8:45am AEST on Tuesday, MailGuard blocked two email scams throughout the day purporting to be from accounting software mainstays MYOB and Xero.
The MYOB scam claimed to be sending recipients a supply order for signature, with a DocuSign link to a malicious .ZIP download.

With the subject 'Your MYOB supply order' the email was sent from randomized names 'via DocuSign' with a reply to: address of the random name, for example, David(dot)Conlan @ myob.com.
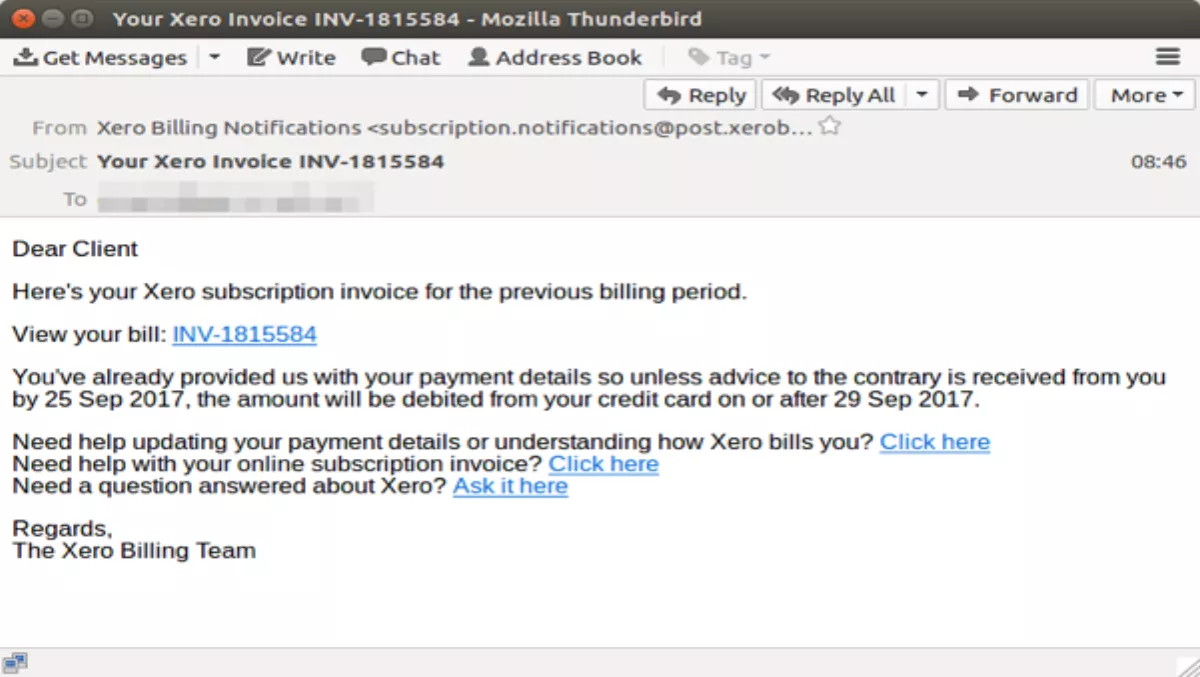
The Xero attack was delivered at the same time as the MYOB scam, and masqueraded as an invoice for your Xero subscription sent from 'Xero Billing Notifications' with a subject that reads 'Your Xero Invoice INV-1815584' in the example below.
Again the link to 'View your bill:' leads to a malicious .ZIP payload.
Not content with the success of the Xero and MYOB scams earlier on Tuesday, from 6:14pm AEST Tuesday, MailGuard began blocking yet another scam targeting Sage accounting which continued into the early hours of Wednesday morning.
Like the Xero attack, the Sage scam imitated a subscription invoice.

The email linked to a compromised SharePoint site hosting a .Zip archive with a malicious JavaScript file.
The display name for the attack was Sage, with a sending and display address of noreply@sageim.com.
The sending domain sageim.com was registered on the 18th of September with a registrar in China.
This morning, the MailGuard team are blocked a brand-new scam pretending to be from an accounting at an accounting practice that links to a fake tax return link with another malicious payload, titled 'Tax return for [name].'
These emails are being sent from a compromised MailChimp account so the sending addresses are unique to each message.
The link is to a benign .docx file hosted on MailChimp, however, the .docx file contains 2 x OLE objects, both of which are CDF documents and can be opened in Microsoft Word or Excel.
The CDF documents themselves contain malicious macros, which are presumed at this stage to download a remote executable.
Finance departments that regularly deal with payments or accounting practices need to be extra cautious what they click this week.


